Information Management & Computer Security(Series) · OverDrive: ebooks, audiobooks, and more for libraries and schools

Advances in Security Information Management: Perceptions and Outcomes ( Computer Science, Technology and Applications: Computer Networks): Guillermo Suarez De Tangil, Guillermo Suarez De Tangil, Esther Palomar: 9781624172045: Amazon.com: Books

M.S. in Business Analytics and Information Management + M.S. in Cybersecurity - Electrical & Computer Engineering
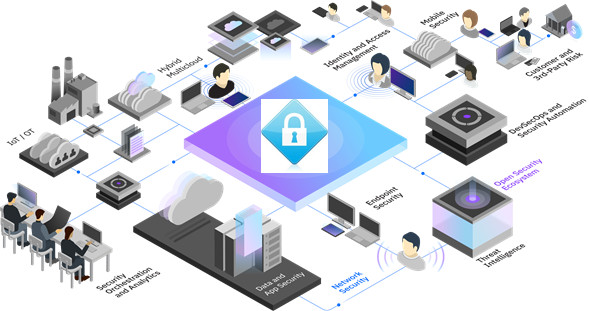
Information Security Management – View through the Digitization lens - ::iExperts Magazine:: Cyber Security - IOT - Big Data - IT Management Technical Articles and more ...